Protecting Your Application in Production
Protecting Your Application in Production
The same technology used to find vulnerabilities early within the SDLC can also be extended into applications running in production environments. If enabled within these environments, attacks against the application layer can be monitored and blocked by Contrast.
In your Community Edition, this feature is already enabled by default. You can see this by navigating to the Policy submenu within the WebGoat application and clicking on the Protect button within it:
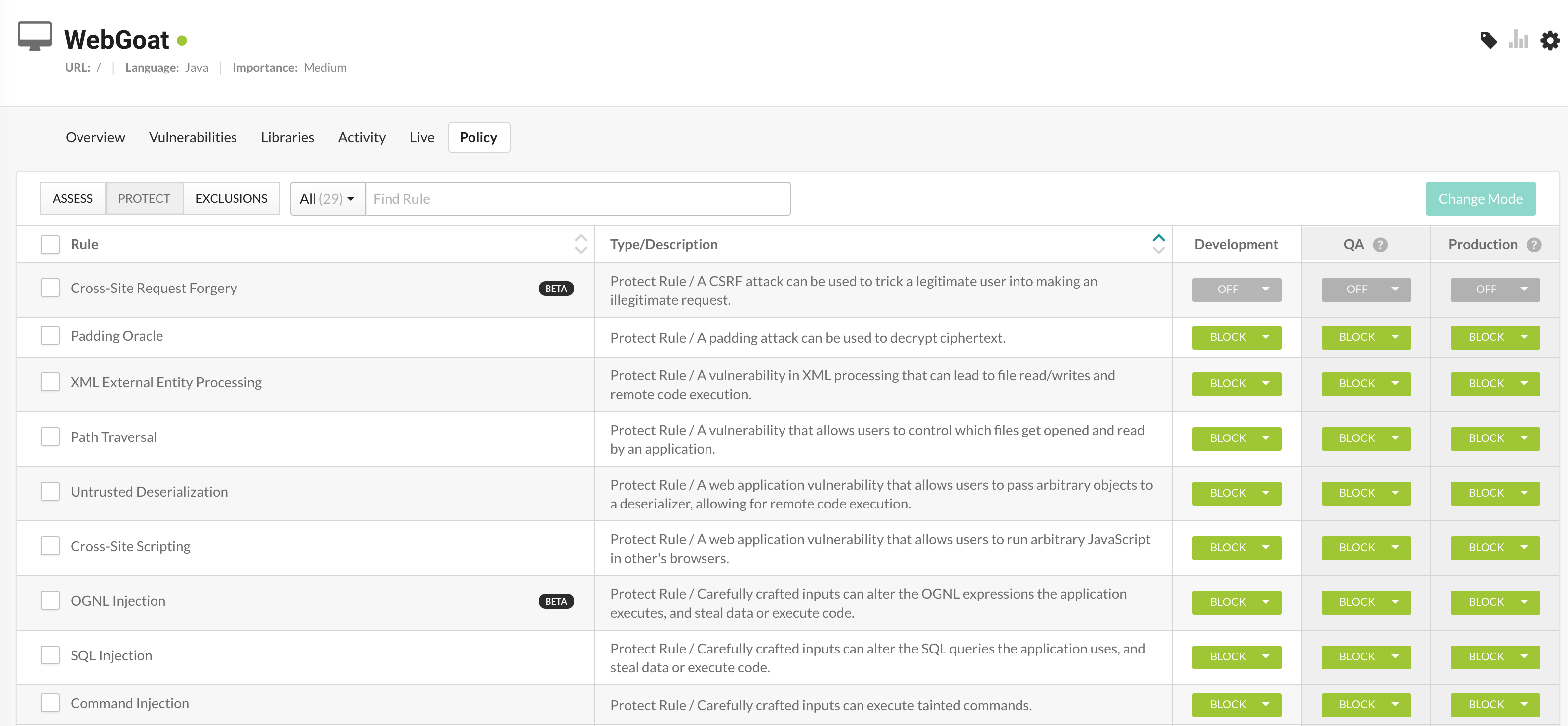
As you can see, Contrast Security is already actively protecting the application from being exploited by many common attacks.
Let’s try attacking the application with exploit designed for the SQL Injection vulnerability that Contrast discovered on the previous step.
- Go back to the WebGoat site and go to
Injection Flaws–>String SQL injection. - Add the following payload into the text field:
Smith' or '98'='98. - Click
Go
Normally, this would result in the entire database being returned back to the calling user. In this case, you will see that no results have found as Contrast is protecting the application.
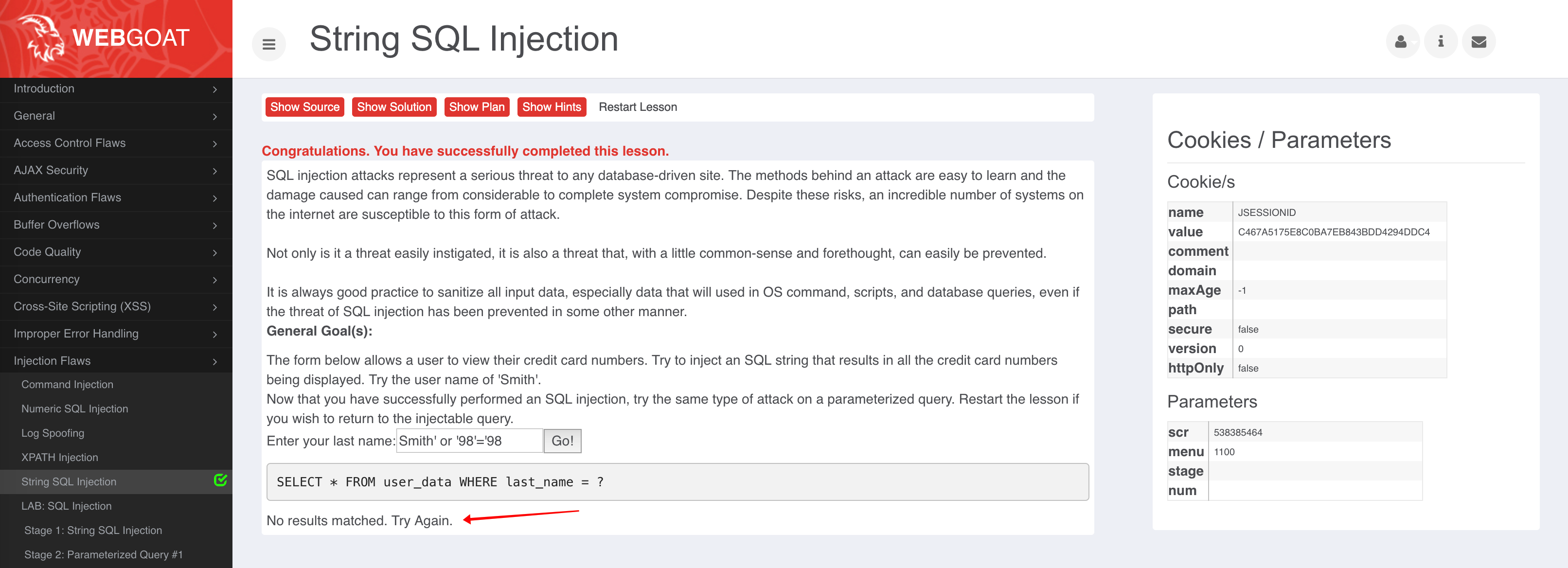
However if you try a regular query like Smith, the request will go through and WebGoat will return some data, so it is not blocking legitimate requests.
Now let’s try to turn Protect off and let’s see what happens. If we go back to Contrast, we can turn off the SQL Injection rule as shown here:
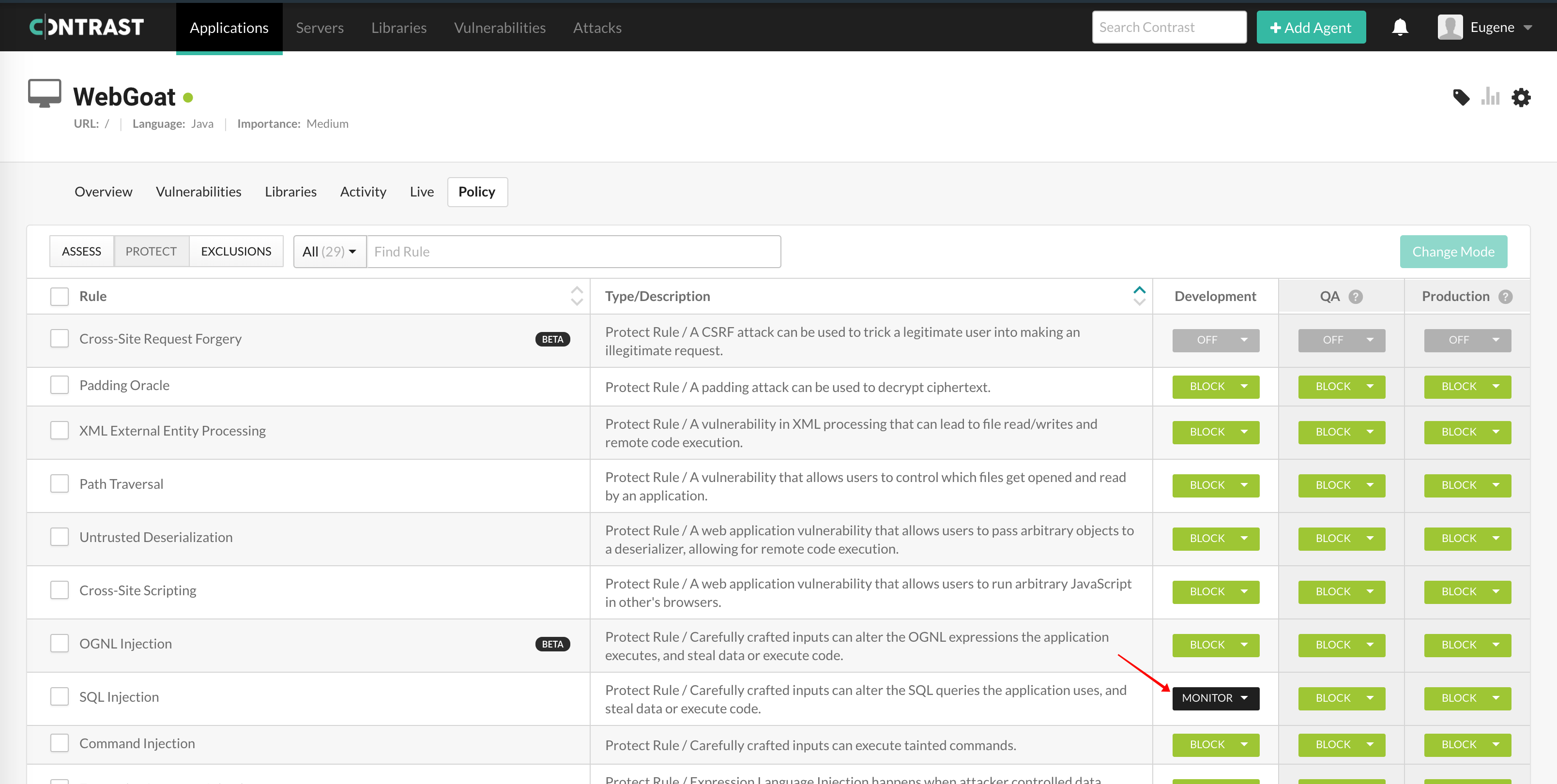
Now you try to exploit WebGoat again and see what happens.