How to discover a new vulnerability
Application Vulnerabilities
In this part we will discover a new vulnerability in Webgoat application and examine the finding in Contrast Security.
It is important to reiterate that Contrast Security identifies vulnerabilities by looking at the normal traffic that goes through the application. With that in mind, let’s identify a SQL injection vulnerability within Webgoat using Contrast.
-
Use the username
webgoatand passwordwebgoatto log into the Webgoat application. -
Navigate to the
Injection Flaws–>String SQL injectionlesson. -
Within the
Enter your last name:textbox, enterSmithor any other string into the field and click onGobutton:
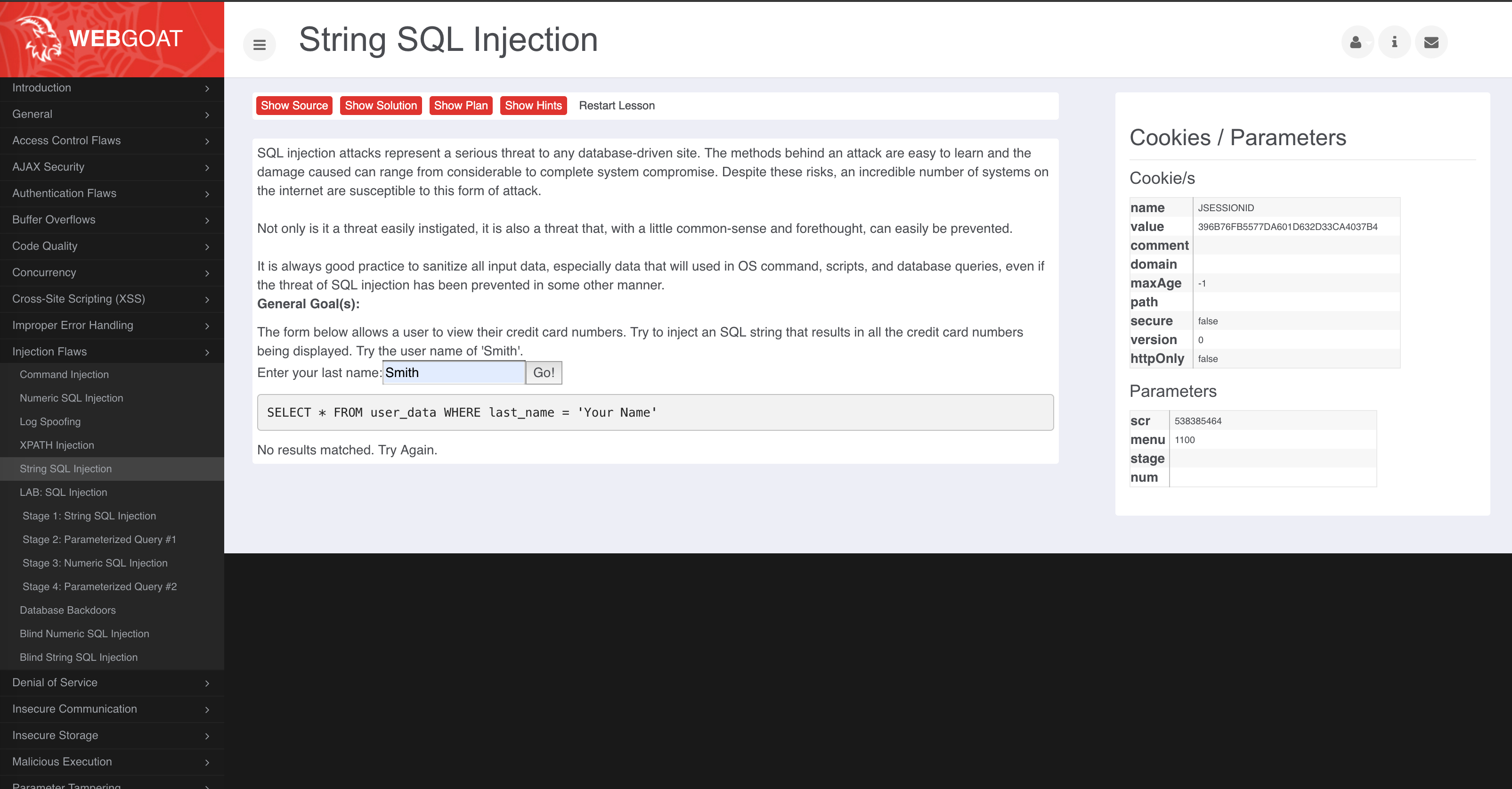
When you perform this action, Contrast is passively monitoring the security of the application including the request made to the application, how that request is handled by the application, and other actions such as queries to the database layer.
- Now switch back to Contrast Security platform and click on V
ulnerabilitiestab within theWebGoatapplication. As you can see, the Contrast agent has identified two new vulnerabilities:Cross-Site Scripting (XSS)andSQL injection.
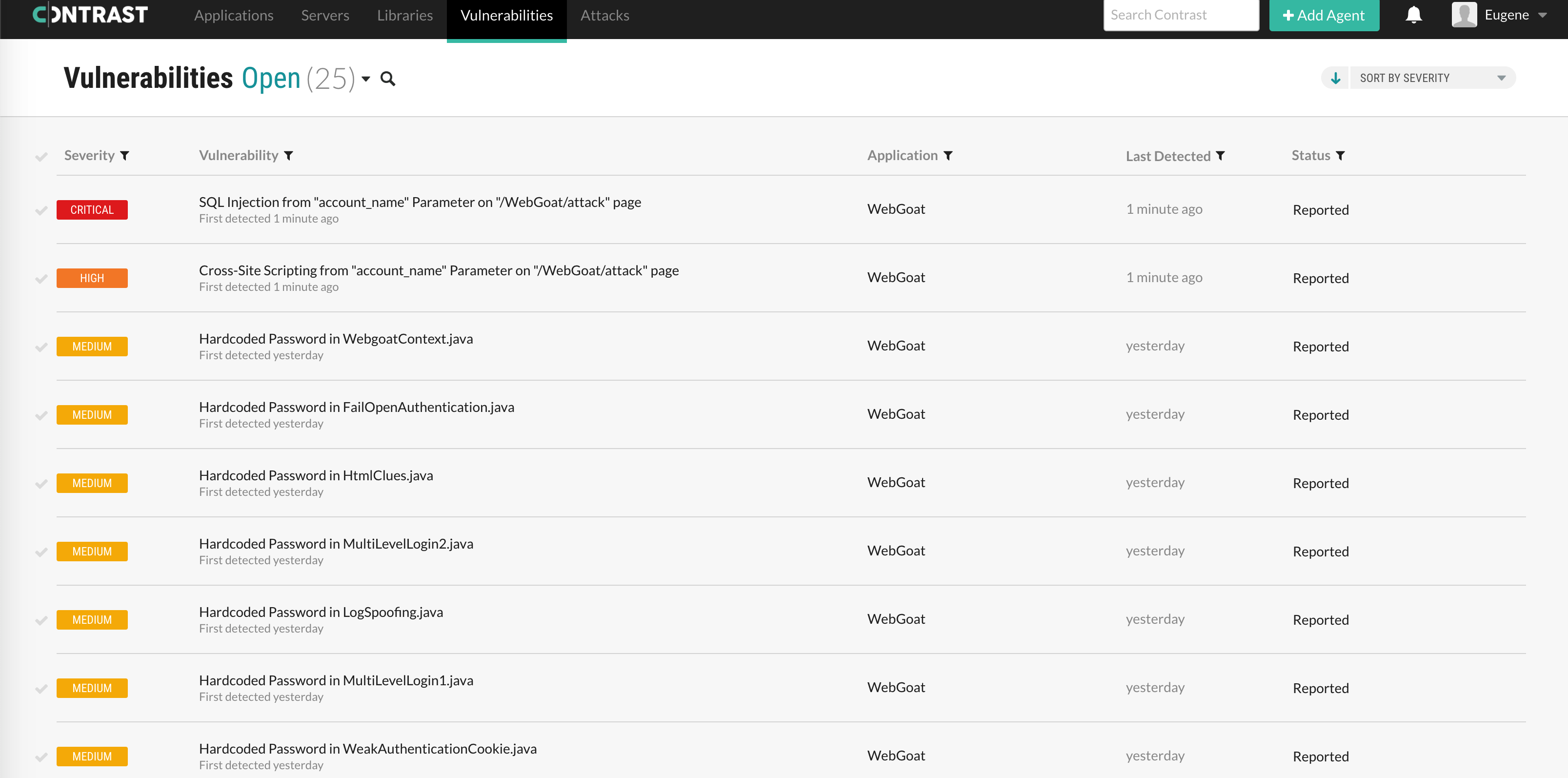
- Click on either of these vulnerabilities to get more detailed information, such as:
Detailsdescribing the data flow of the vulnerability fromsourcetosinkincluding anypropagators.HTTP Infothat shows the query string parameters, request body, and headers associated with the request.How to Fixinformation providing different approaches to remediating this type of vulnerability.